Recently I happened to work in an Angular upgrade work and came across this message after doing the npm installations.
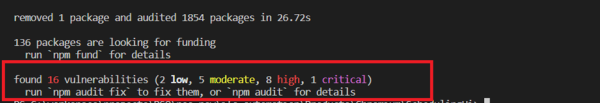
You may have come across this message if you have worked in any kind of Javascript framework/ environment like Node js/React/Vue. After checking a bit found that it is a feature introduced with npm v6. Npm scans through our dependencies to check for possible security vulnerabilities that exist in our dependency tree. It checks our current installed package versions (in package.json and package-lock.json) against known security risks reported in public npm registry and provides a summary report as above.
How to fix the issues
Obviously, it is not a good idea to provide a code with known security vulnerabilities. Hence, below are a few suggestions to fix the issues.
- Get a detailed report of the security vulnerabilities with npm audit
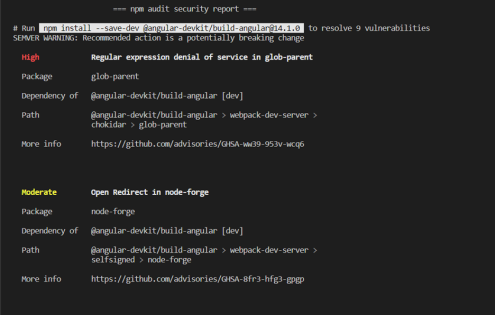
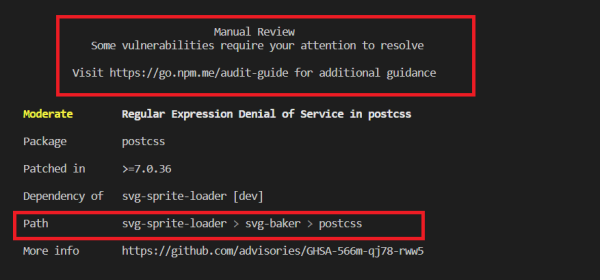
It will show in which package you have the issue, severity, and the path of package in dependency tree. Moreover, apart from that some of the vulnerabilities may show a command to resolve the issue as well.
- As we are more concerned about the security vulnerabilities in production dependencies, use npm audit –production command to check for prod dependencies directly. If there are no vulnerabilities, you are good to go.
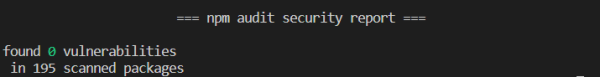
- Else, to resolve the vulnerabilities automatically run npm audit fix command. As a result, it will execute a npm install command under the hood and will upgrade patch versions of the packages with issues.
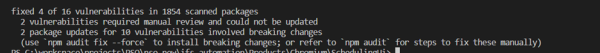
In my case there are still some vulnerabilities to be fixed manually. As suggested npm audit –force will upgrade dependencies with issues to major version. Hence, this may cause breaking changes in the code. Therefore, it is not advisable to apply this command without taking a closer look.
- Try running npm update command. It will update all the package minor versions to the latest and may fix potential security issues.
- If you have a vulnerability that requires manual review, you will have to raise a request to the maintainers of the dependent package to get an update. For the below vulnerability, changes are expected in svg-baker package to refer to a postcss version higher than 7.0.36. Nevertheless, in the worst case, if the package is not maintained anymore, you will have to do the update yourself.
Want to solve complex technical issues and bring solutions?
Join IFS today: Careers | IFS